PRC State-Sponsored Cyber Actors Deploy BRICKSTORM Malware Targeting Public Sector and Information Technology Systems
Affected organizations are primarily in government services and information technology sectors. BRICKSTORM’s self-monitoring function ensures automatic re-installation if disrupted.
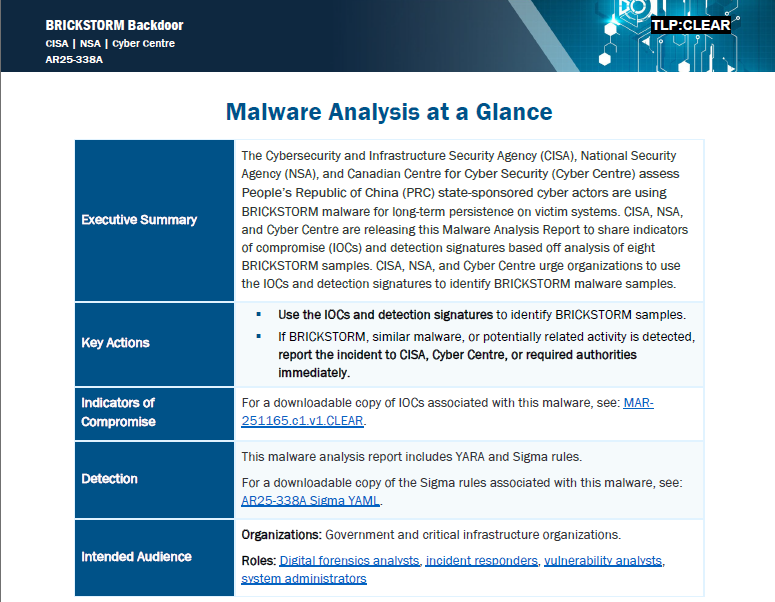
UNITED STATES — The Cybersecurity and Infrastructure Security Agency released an alert detailing intrusions by People’s Republic of China state-sponsored actors using BRICKSTORM malware.
This backdoor targets VMware vSphere and Windows environments to establish long-term persistence. The malware enables stealthy access through multiple encryption layers and facilitates lateral movement within networks.
Affected organizations are primarily in government services and information technology sectors. BRICKSTORM’s self-monitoring function ensures automatic re-installation if disrupted.
The alert highlights ongoing compromises where actors obtain legitimate credentials by capturing system backups or Active Directory data. They exfiltrate sensitive information and target VMware platforms to steal virtual machine snapshots for credential extraction.
In one confirmed case, intruders accessed a web server in the demilitarized zone before moving to an internal vCenter server to implant the malware. Seven additional BRICKSTORM samples show variations in capabilities, underscoring its adaptability. Communications are concealed using DNS-over-HTTPS and SOCKS proxies.
Intruders employ advanced tactics to evade detection, including nested TLS encryption and WebSockets. Persistence mechanisms allow the malware to restart automatically upon interruption.
BRICKSTORM is a custom ELF Go-based backdoor for stealthy access, persistence, and command and control. It uses self-watching for reinstallation if disrupted, multiple encryption layers like HTTPS, WebSockets, and nested TLS. DNS-over-HTTPS mimics web traffic with public resolvers such as Cloudflare, Google, and Quad9.
Interactive shells, file manipulation, and SOCKS proxy enable lateral movement. Some samples act as SOCKS proxies or use VSOCK for virtual machine communication with self-signed certificates.
Analysis of eight samples reveals variants for VMware vSphere and Windows. The joint Malware Analysis Report provides indicators of compromise and detection signatures. Network defenders are urged to scan for BRICKSTORM using provided YARA and Sigma rules.
Actors gain access via web shells, move laterally using RDP and SMB with service accounts, copy Active Directory databases, escalate via sudo, and drop BRICKSTORM in /etc/sysconfig/. Modifications to init files ensure execution on boot.
In a detailed incident, access began in April 2024 and persisted through at least September 3, 2025. Lateral movement included jump servers and Active Directory Federation Services for key exfiltration.
Blocking unauthorized DNS-over-HTTPS providers is recommended to reduce unmonitored traffic. Inventory of network edge devices should include monitoring for suspicious connectivity.
Proper segmentation restricts traffic from demilitarized zones to internal networks. If similar activity is detected, incidents should be reported to the agency’s operations center. The guidance emphasizes hunting for intrusions and applying mitigations promptly. Critical infrastructure operators face heightened risks from such state-sponsored activities.